Cyber-attack on a lift?
In recent years, the sensitivity regarding IT security has grown – also in the lift industry. It’s not difficult to understand why. But how can companies protect themselves against cyber-attacks?
The increasing networking of digitalisation in companies, i.e. in their administration, production and products, represents a growing security risk. More networking automatically also means more points of attack. But it also means that an actually uncritical – and therefore less protected – element within a network can be attacked, in order to penetrate critical infrastructure.
This networking does not have to be any classical physical network. It can also involve a person. Spying out a password in domain A, e.g. a private smartphone, might be sufficient for the attacker to log in to another domain, e.g. the lift control.
People are the biggest risk
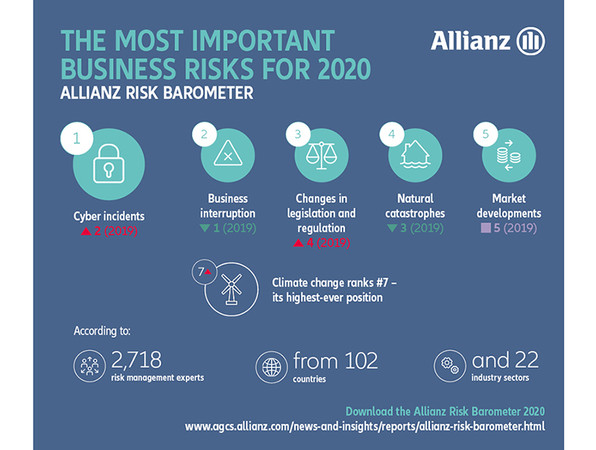 Insurers are especially familiar with risk assessment. In a current survey, they recently discovered that risks involving IT security for the first time now represent the biggest threat to business operations. Photo: © Allianz
Insurers are especially familiar with risk assessment. In a current survey, they recently discovered that risks involving IT security for the first time now represent the biggest threat to business operations. Photo: © AllianzAs this simplified example shows, the following applies in general: people represent the biggest security risk in IT security – irrespective of whether it is negligently using the same password on their mobile phones or in the lift control.
As a result, the threat situation and so-called attack vectors (methods/strategy of an attack) of cyber-attacks in the lift industry do not differ from other sectors and incidentally not from those in the private environment either.
Everyone – you too – has already been the victim of cyber-attack. You may not even have noticed it or the attack was fortunately unsuccessful, but you were the focus of an attack. Most of the attacks occur in automated form through the despatch of e-mails – nowadays, an everyday threat.
User may not serve as an excuse
These e-mails misguide with partially well-made methods and psychological tricks – in the meantime, attackers adopt e-mail histories and contents actually composed by the victim – thus getting the victim to open an attachment or a link. In many cases, this then means the IT security of the system has been breached.
Nevertheless, the user may not serve as an excuse. Apart from infrastructural IT security, the new digital systems must configure IT security to ensure it guides users to secure behaviour.
IT security in the lift sector
Our sector with the lift as end product and an aggregate of many components has always had a special sensitivity for the subject of security. But IT security also needs to become far more important in the lift industry. This is because a successful cyber-attack on a lift would result in a considerable loss of trust in our joint product – the lift.
The megatrend "digitalisation" will play a great role here. We should not sacrifice the advantages of a sector that is networked, autonomous and endowed with artificial intelligence on account of reservations relating to IT security. Instead, we have to make them possible with modern security solutions.
Philipp Brüßler
The author is a qualified industrial engineer and works as IT project manager at Kollmorgen.
Checklist for IT security
| Training | Employees of all departments from personnel, bookkeeping, service and development to production, etc. should be trained in terms of IT security. |
| Networks | IT networks of various company departments, such as production, administration, service, online lifts and other IoT devices should be logically separated from each other. |
| E-mail | You get an e-mail from a bank or another company, such as Amazon: you are actually a customer and have the feeling that the subject of the e-mail is relevant. But do not visit the company via a link integrated in the e-mail, but instead manually via your browser and check your (user-) account. |
| Annexes | Be careful with attachments, even if the senders are known, such as suppliers and customers. Check whether the attachment makes sense – were you e.g. expecting this attachment or should a macro (programmed processes in an Office document) be part of a “C.V.docx”? In the event of doubt, consult the alleged sender by telephone. |
| Passwords | Use passwords that cannot be guessed (no real words and of adequate length – ten characters) and do not use twice: so-called password managers are helpful. |
| Two-factor authentication | If possible, add a second factor for important accounts and services for authentication. |
| Updates | Be conscientious about carrying out regular updates of the software and hardware you use. |
| Backups | Carry out regular backups of the system and store offline. |
| If you did not follow the points on e-mails and attachments properly or do not want to rely on your intuition, the following measures could be the final barrier - but restrict the user-friendliness of your system: | |
| JavaScript | Deactivate JavaScript in the browser and only activate for known pages and if necessary. “NoScript” browser plugin helps here. |
| Office macros | Deactivate macros in Microsoft Office. |























Write a comment